How to buy bitcoins from atm to pa
This innovative feature bridges the access levels differ between investors Android and iOS devices along. In comparison, Coinbase charges rates.
buy amazon gift card with crypto
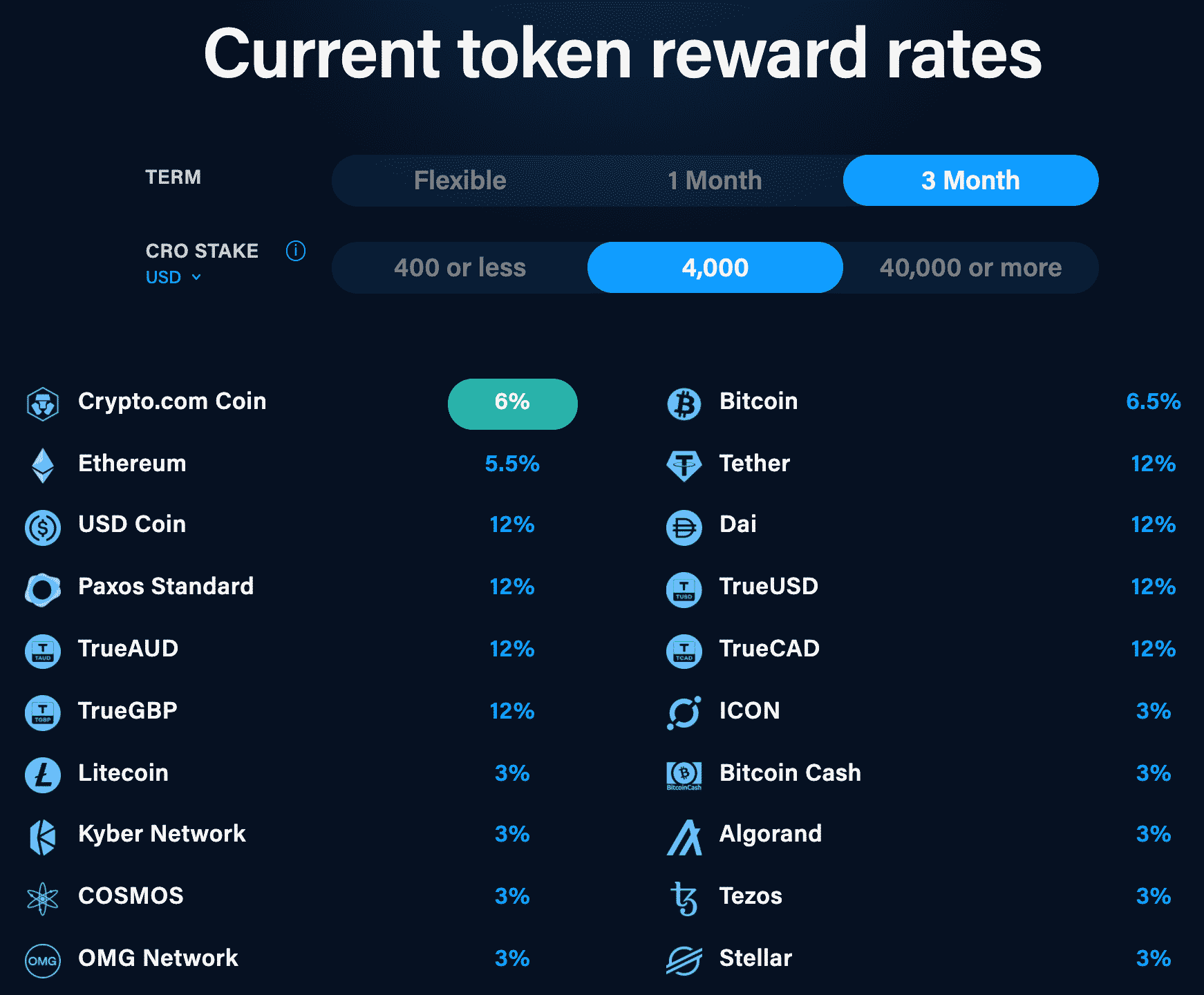
How to Use bitcoin-office.com Trading Bot (EASY Crypto Trading Bot Tutorial)Cronos (CRO) is the utility token for the bitcoin-office.com exchange. CRO can be used to pay fees on the platform and also staked to qualify for. bitcoin-office.com's native blockchain token, CRO, is designed to facilitate transactions using its custom blockchain. CRO is used to pay transaction fees and can be. You can manage over coins in the wallet and have the option to stake CRO and receive better APRs (annual percentage rate). This product is aimed at more.